What is Vendor Risk Management: A Complete Guide + Examples
As organizations rely more heavily on third-party vendors, the risk surface expands and becomes harder to control.
To put it in perspective, a report by the Pokemon Institute revealed that third-party vendors are linked to 73% of data breaches.
And that’s just one layer of vendor risk.
Vendor ecosystems are becoming increasingly complex and risky. That’s why it’s super important to have a structured, proactive approach to vendor risk management.
An effective VRM program helps you protect sensitive data, maintain regulatory compliance, prevent costly disruptions and build more resilient vendor relationships.
In this guide, I’ll break down what vendor risk assessment and management is, why it’s so important and how to build a scalable program that protects your business. I’ve also included examples, best practices, tools and templates to get you started.
Table of Contents
- What Is a Vendor Risk Assessment?
- Why Vendor Risk Management Is Non-Negotiable
- Types of Vendor Risk to Assess
- Vendor Risk Assessment Checklist
- How to Conduct a Vendor Risk Assessment
- Risk Scoring Matrix: How to Prioritize What Matters
- Real Examples of Vendor Risks
- Vendor Risk Assessments FAQs
Quick Reads
- A vendor risk assessment is the process of evaluating potential threats that third parties, such as vendors, suppliers, contractors or partners, may pose to your organization.
- An effective vendor risk management program prevents data breaches and supply chain attacks, protects business continuity, improves visibility and transparency across teams and supports better decision-making throughout the vendor lifecycle.
- The different types of vendor risk include cybersecurity risk, compliance risk, operational risk, financial risk, reputational risk, safety risk and strategic risk, among others.
- Follow these steps to conduct a vendor risk assessment: identify critical assets and vendors, understand the different types of risks and define your criteria and risk thresholds.
- Then gather vendor information, generate security ratings, send out questionnaires, tier your vendors, develop a risk management plan, perform annual assessments and report vendor performance with clear, visual insights.
- Use a risk scoring matrix to evaluate each vendor by rating the likelihood of a risk occurring and its potential impact on your business.
- Real-life examples from Slack, Zoom and Target show how third-party vendors can introduce serious cybersecurity, compliance or operational risks into an organization.
- Visme comes packed with a robust set of features and tools to streamline your vendor risk management process.
- Collect assessment data, deliver insightful reports and drive informed decisions with professionally designed templates, intuitive features, powerful data visualization tools and a wide range of AI-powered tools.
What Is a Vendor Risk Assessment?
Vendor risk assessment is the process of evaluating potential threats that third-party vendors, suppliers, contractors or other business partners may pose to your organization.
As more businesses rely on external providers for software, infrastructure and essential services, this due diligence process shields organizations from downstream risks.
The assessment typically covers the entire vendor lifecycle from initial sourcing and onboarding to ongoing monitoring and offboarding.
It involves gathering data on a vendor’s security controls, privacy practices, financial health and operational reliability, often through standardized questionnaires, risk scoring models and due diligence checks.
Once the team has identified the risks, they analyze and prioritize them based on their likelihood and potential impact. Then, they map the results to relevant regulatory frameworks, such as ISO, NIST or GDPR, to ensure they are aligned with industry standards and compliance requirements.
Why Vendor Risk Management Is Non-Negotiable
Even if your internal controls are airtight, working with vendors who lack strong security or compliance practices can open the door to data breaches, regulatory violations and costly operational disruptions.
This risk grows even more critical when vendors have access to sensitive, proprietary or regulated data.
A strong VRM program offers a structured, repeatable and transparent way to assess and mitigate third-party risks at every stage of the vendor lifecycle.
Here are a few more reasons VRM is a must-have for companies of all sizes:
1. Prevents Data Breaches and Supply Chain Attacks: Vendors are one of the most common sources of cybersecurity incidents. A robust VRM program helps identify vulnerabilities early, enforce security standards and continuously monitor vendor risk. This reduces the chances of breaches before they escalate.
2. Ensures Compliance with Regulatory Requirements: Regulators are tightening requirements around third-party risk. According to Gartner, 60% of organizations work with more than 1,000 third parties, many of which are subject to strict frameworks such as GDPR, HIPAA, PCI-DSS or CCPA. A consistent VRM process helps you vet vendor compliance, document oversight and minimize the risk of non-compliance, audits and fines.
3. Protects Business Continuity: According to Deloitte, 87% of organizations have experienced an incident with a third-party vendor that disrupted their operations. VRM ensures every team involved in vendor onboarding, monitoring and offboarding follows a structured process. This proactive approach helps minimize downtime and keeps operations stable when disruptions happen.
4. Improves Visibility and Transparency Across Teams: A centralized VRM system gives legal, IT, procurement and other business units shared visibility into vendor risk. With access to real-time risk profiles and performance metrics, teams can collaborate more effectively, resolve issues faster and make smarter, organization-wide decisions.
5. Supports Smarter Vendor Selection: Third-party vendor risk assessments during the procurement phase help you avoid high-risk partners from the start. A structured VRM process helps procurement teams spot red flags and select vendors that align with your compliance needs, service-level expectations and overall risk tolerance.
6. Reduces Financial and Legal Exposure: One vendor misstep can lead to lawsuits, regulatory fines or lost revenue. IBM Security reported that the average cost of a third-party data breach in 2023 was $4.45 million. Proactive vendor evaluation lowers exposure to this risk by identifying red flags early, avoiding non-compliant vendors and enforcing contractual protections.
Types of Vendor Risk to Assess
Staying ahead of third-party threats means paying attention to a broad range of risk categories throughout the vendor lifecycle.
Here’s a breakdown of the major risk categories to watch out for, along with practical examples to put each one into context.
| Risk Type | What It Includes | Practical Example |
| Cyber Risk | Exposure to cyberattacks, malware, phishing or ransomware due to poor vendor cybersecurity practices | A vendor’s compromised network spreads ransomware into your internal systems |
| Information Security Risk | IT vendor risks tied to data loss, unauthorized access or weak controls over sensitive data like PII or trade secrets | A third-party HR tool leaks employee social security numbers due to weak authentication settings |
| Legal Risk | Legal liability stemming from data breaches, weak contracts or violations of regulations tied to third-party vendors | A vendor mishandles patient records, but your contract lacks a data protection clause, leaving you liable |
| Compliance & Regulatory Risk | Failure to comply with laws like GDPR, HIPAA and PCI-DSS due to vendor negligence or lack of proper vetting | Your payment processor stores cardholder data in violation of PCI-DSS, triggering an audit and penalties |
| Reputational Risk | Damage to your brand due to unethical vendor behavior, poor security practices or negative media exposure | Your vendor suffers a high-profile breach that becomes public, affecting customer trust in your brand |
| Operational Risk | Interruptions or performance issues caused by vendor outages, staff shortages or poor delivery timelines | A SaaS vendor experiences prolonged downtime, halting internal workflows for days |
| Financial Risk | Exposure to vendor bankruptcy, missed payments or financial instability impacting the delivery of services | A financially unstable vendor folds mid-contract, disrupting a critical digital transformation project |
| Strategic Risk | Misalignment between vendor priorities and your long-term business goals | A vendor pivots to serve a different industry, cutting back on support for your specialized needs |
| Privacy Risk | Improper handling or sharing of personal data by vendors, leading to breaches or privacy law violations | A marketing partner sends unsolicited emails using scraped customer data, violating data protection laws |
| Subcontractor / Fourth-Party Risk | Risks introduced by vendors’ third parties, which you don’t directly manage or monitor | Your data center vendor outsources maintenance to a subcontractor that lacks security certifications |
| Geopolitical / Location Risk | Risks related to operating in politically unstable or sanctioned regions or cross-border compliance complexities | A vendor located in a newly sanctioned country becomes legally restricted from doing business with you |
Vendor Risk Assessment Checklist
Finding the right vendor requires looking beyond price tags.
Your vendors become extensions of your business with access to sensitive data, core systems and a host of other business functions.
During the third-party risk assessment process, you want to gauge factors like trust, security posture, compliance standards and long-term stability as well.
This comprehensive checklist helps you assess potential or existing vendors across six key areas, including cybersecurity, compliance, financial stability and more.
You can either download and share it with your team members to fill it out by hand. Or generate a live URL to review it virtually with your team during onboarding, annual reviews or when conducting vendor due diligence.
Made with Visme
How to Conduct a Vendor Risk Assessment
Here's a step-by-step guide to help you conduct a vendor risk assessment effectively.
Made with Visme Infographic Maker
1. Identify Critical Assets and Vendors
Right from the start, you need to be clear on which assets matter most to your business and which vendors have access to them.
Otherwise, you’ll end up wasting time evaluating low-impact partners while high-risk vendors fly under the radar.
Start with your critical assets. These are the systems, data and services that, if disrupted or exposed, would materially affect your ability to operate.
You’re looking for things like:
- Core infrastructure (cloud providers, hosting environments, APIs)
- Customer-facing platforms (CRMs, payment processors, e-commerce tools)
- Sensitive data stores (PII, PHI, IP, financial records)
- Communication and collaboration tools (email, Slack, HR systems)
Once you’ve mapped those out, shift focus to the vendors that support them. This list could include:
- Direct providers (core service providers like cloud storage, CRM platforms, or payroll systems, email and domain hosting)
- Indirect vendors (e.g., subcontractors, resellers and maintenance providers )
- Specialized providers (e.g., niche compliance consultants, penetration testers)
It’s not always obvious who’s “mission-critical” until you trace the full dependency chain.
For example, Target’s 2013 data breach wasn’t caused by a payment provider; it originated from an indirect vendor—a third-party HVAC company with privileged network access.
To make this step actionable, bring your IT, legal, procurement and security teams together to run a business impact analysis (BIA). This exercise helps you understand:
- Which systems and services are essential
- What level of access each vendor has
- The types of data being shared (and where it flows)
- Potential operational or reputational fallout from a vendor incident
You don’t need complex tools to map these relationships—a structured Excel sheet or Airtable base can do the job just fine.
Start by creating a simple tracker with fields like:
- Vendor Name
- Services Provided
- Access Type (e.g., read-only, admin, API access)
- Systems Touched (e.g., CRM, billing platform)
- Data Sensitivity (e.g., PII, financial, confidential IP)
This table becomes the foundation for every decision that follows.
2. Understand the Different Types of Risks
The next step is to get specific about the kinds of risks you’re exposed to.
The goal here isn’t to create a generic list of potential threats. It’s to map out the risk categories that actually matter within the context of your business operation.
Start by considering your operating model, regulatory landscape and the nature of the vendor relationship.
- Are you in a highly regulated industry, such as finance or healthcare? Then, compliance and data privacy will likely be at the top of the list.
- Relying on a SaaS provider for customer onboarding? Then, cybersecurity, availability and third-party dependencies should be your main focus.
- Supporting global operations? Geopolitical and reputational risks require closer attention.
This is where many teams fall short. They either assume all risks apply equally or use a one-size-fits-all checklist that doesn’t reflect their environment.
The best approach is to conduct a vendor risk scoping exercise, involving:
- A workshop or working session with stakeholders from InfoSec, Legal, Procurement and IT to map out what risks are relevant to different types of vendors.
- Contextual reviews of your vendors' services, role, access level and exposure.
- Aligning this step with any existing enterprise risk management (ERM) or internal audit frameworks, so vendor risk isn’t treated in isolation.
To guide this process, refer back to the vendor risk assessment checklist we shared earlier in this guide.
As Gianluca Ferruggia, General Manager of DesignRush, advises:
“I advise going beyond a straightforward checklist when creating a vendor risk assessment and including qualitative information from in-person discussions with vendors to comprehend their financial stability, business continuity plans, and cultural fit. This assists in identifying dangers that are not immediately apparent from regular questionnaires.”
This kind of qualitative, context-driven review is essential for uncovering hidden risks and making well-rounded decisions.
Jeff Kaiden, CEO of Capacity, echoes this perspective from a leadership lens:
“Vendor risk assessments need more than just a checklist. Of course, we check for insurance, financial stability, and regulatory compliance. But we also look at things that are harder to measure—how quickly vendors respond, whether their company culture fits with ours, and how transparent they are when something goes wrong. We get feedback from teams who deal with vendors directly, not just the procurement department.”
Once you’ve matched each vendor to their relevant risk categories, tag them accordingly in your vendor inventory (you’ll formalize this further in Step 7).
From here on, everything you do—from setting risk criteria to sending questionnaires—should tie back to these scoped risk categories.
3. Define Your Criteria for Assessing Risk, Scope, Boundaries and Risk Acceptance Levels
You can’t manage vendor risk effectively without setting clear rules of engagement.
That means defining how you’ll assess vendors, what you’ll include in the process, where your limits lie and how much risk your organization is willing to accept.
Criteria for Assessing Risk
our criteria act as the lens through which you’ll evaluate each vendor. For every risk category in scope — whether cybersecurity, compliance, financial health, or operational continuity — define the specific signals or standards you’ll measure.
If vendors integrate through APIs, align with your IT team on shared risks. You can share this concise primer on securing business APIs to ensure everyone’s on the same page.
Let’s say you’re evaluating cybersecurity risk. Some of your assessment criteria might include:
- Existence of a SOC 2 Type II or ISO 27001 certification
- Use of MFA (multi-factor authentication) and endpoint protection
- History of reported breaches or security incidents
- Vendor's security architecture (cloud vs. on-prem, segmentation, etc.)
To avoid reinventing the wheel, use trusted frameworks to guide your criteria, like:
- NIST 800-53 or Cybersecurity Framework (CSF) for technical controls, access management, incident response, and continuous monitoring
- ISO/IEC 27036 for supplier relationships
- Shared Assessments SIG (Standardized Information Gathering) for building detailed security risk questionnaires.
Define the Scope of Your Assessment
Scope answers an important question: What exactly are we reviewing?
Define the specific aspects of the vendor relationship under review. Are you evaluating:
- The vendor’s internal security practices?
- Their subcontractors and downstream service providers?
- The systems or data they interact with?
Also, clarify the timing and lifecycle of the assessment:
- Is it just during onboarding?
- Will you review them annually or when there’s a material change in service?
- Does contract renewal trigger a reassessment?
Set Boundaries and Information Limitations
You won’t always get full visibility into a vendor’s operations, especially with large-scale providers or small businesses with limited resources. That’s where defining boundaries comes in.
Boundaries may include:
- Which documents you can reasonably request (e.g. audit reports, security policies, insurance certificates)
- The controls within your scope (e.g. you can assess their patching cadence, but not test their codebase)
- How deep you can access sub-tier suppliers or offshore partners
Set realistic expectations so your team doesn’t waste time chasing inaccessible data. At the same time, note red flags. If a vendor flat-out refuses to share anything meaningful, that’s a risk in itself.
Risk Acceptance Levels
Not every vendor will check every box and that’s expected. The question is: how much risk are you willing to tolerate?
Risk acceptance levels vary by organization, but they generally fall into three tiers:
- Acceptable: Vendor meets all standards, no action needed;
- Tolerable with mitigation: Gaps exist, but can be managed with compensating controls, contract clauses or added monitoring.
- Unacceptable: Risk exceeds threshold; vendor must remediate issues or be replaced.
It’s also important to clarify:
- Who decides what’s acceptable? (e.g. IT Security Manager, Head of Legal, CFO?)
- What’s the escalation process for high-risk findings?
- Do certain risk levels require executive approval or board notification?
Some organizations use weighted scoring models to quantify this. Others rely on qualitative risk summaries.
Either way, the end goal is the same: build a risk assessment matrix that supports fast, defensible calls on whether to proceed, mitigate or walk away. (More on that below)
4. Gather Information About the Vendor’s Product and Risk Profile
This phase is where you’ll collect the intel you need to understand:
- What risks the vendor might introduce based on what they do
- How they operate and
- How their product or service connects to your organization.
Start by collecting essential information about the product or service itself.
- What exactly does the vendor offer?
- How are products developed, maintained and supported
- How is it deployed: on-prem, cloud-based, hybrid?
- What data does it handle?
- Is it integrated with your systems or is it used in isolation by a specific department?
- What potential vulnerabilities can the product or process introduce?
Many teams skip over this level of detail, assuming it’s obvious, but risk lives in the nuance.
Next, request operational and security documentation that sheds light on how the vendor manages their infrastructure and processes. This typically includes things like:
- Data flow diagrams
- Security whitepapers
- Compliance reports (SOC 2, ISO 27001, PCI DSS, HIPAA if relevant)
- Incident response plans and past incident reports
- Infrastructure and hosting architecture
- Subprocessor or third-party vendor lists
Depending on the potential risk level of the vendor, you may also request their
- Business continuity plan or disaster recovery plan
- Scenario planning or tabletop exercise summaries (for critical vendors)
- data retention or disposal policies
- Software development lifecycle (SDLC) documentation.
For high-risk vendors, you’ll want to go deeper, especially if they handle customer data, have administrative-level access to your systems, or are classified as business associates required to comply with BAA security obligations, including data access controls, breach notification requirements, and accountability.
To keep things organized, arrange your findings in a simple table like this:
| Information Category | What to Collect |
| Product Functionality | Description of service, features and delivery model |
| Data Handling | Types of data accessed or processed |
| Hosting & Architecture | Cloud provider, data residency, multi-tenancy |
| Security Practices | MFA, encryption, patching cadence, security org chart |
| Compliance Certifications | SOC 2, ISO 27001, HIPAA, etc. |
| Subprocessor Relationships | List of subcontractors or fourth parties |
| Breach History & Reputation | Past incidents, lawsuits, negative press |
You don’t need a heavy-duty tool for this. Use structured intake forms, shared templates, or lightweight tools like Airtable or Google Sheets to build a scalable, searchable tracker that keeps all vendor documentation in one place.
Pro Tip: Don’t wait until vendor onboarding to gather this information. Start earlier, ideally during the procurement or sourcing process. That way, you can flag risk before a contract is signed, not after your data is already exposed.
5. Generate Security Ratings
Security ratings provide a quick and objective assessment of a vendor's security posture, based on publicly available data.
These ratings are generated by third-party platforms that scan the vendor’s internet-facing infrastructure for known risk signals, such as expired certificates, open ports, insecure configurations or exposed credentials. They help you spot red flags early, especially when vendor documentation is incomplete or delayed.
Three of the most widely used platforms in this space are:
- BitSight
- SecurityScorecard
- RiskRecon
Each of these tools scans a vendor’s public-facing infrastructure and assigns a letter grade or numerical score, usually from 250 to 900 or A through F.
You can benchmark vendors against others in the same industry, track changes over time and receive alerts if a vendor’s score drops, indicating a new issue has surfaced.
Here’s a simplified example of how that data might look:
| Vendor Name | Security Score | Common Issues Identified |
| Vendor A | 780 (A) | None |
| Vendor B | 580 (C) | No DMARC, unpatched systems |
| Vendor C | 640 (B) | Leaked credentials, weak SSL |
Security ratings aren’t definitive, but they are useful for triaging risk.
A low score doesn’t mean automatic disqualification, but it may warrant a deeper follow-up in the next steps. A high score, on the other hand, can validate a vendor’s claims and reduce your due diligence time.
Pair them with the documents and answers you collected in Step 4. If the score reveals an issue you didn’t catch earlier, you can use that as a trigger to request more information or flag the vendor for a follow-up audit.
6. Send Out Security Questionnaires
Security questionnaires help you validate a vendor’s internal controls, going beyond what’s visible externally. You can use either a standard framework or a custom form tailored to your specific risk categories.
For most organizations, the goal is to assess:
- How the vendor handles sensitive data
- What controls are in place for access and authentication
- Their security governance, policies and certifications
- Their incident response and business continuity practices
Use this ready-made vendor security questionnaire as a starting point
If you’d rather avoid juggling spreadsheets or paper forms and chasing email replies, Visme Forms offers a streamlined, automated way to collect responses.
You can:
- Build custom forms with dropdowns, yes/no options and file upload fields
- Embed clarifying notes, tooltips or visual guidance for more complex questions
- Add branding and conditional logic to tailor the form based on the vendor type
- Share it securely via a unique link and track submissions in one central place
Once responses are in, review them for alignment with your risk criteria. Flag any incomplete answers, vague policies or gaps in control maturity. For higher-risk vendors, request supporting documentation, such as SOC 2 reports or policy samples, to verify key claims.
7. Establish a Vendor Inventory and Tiering Model
Once you’ve gathered relevant information about each vendor’s service, data access and risk profile, the next step is to classify them based on the level of risk they pose to your organization. That’s the job of a vendor tiering model.
Vendor tiering is about assigning the right levels of scrutiny to each vendor based on business impact and risk exposure.
This exercise lets you focus your time and resources where they matter most, without bogging your team down with deep assessments of low-risk suppliers.
Most organizations use a three-tier model to keep things simple and scalable:
| Tier | Risk Level | Description | Example Vendors |
| 1 | High | Vendors with access to sensitive data, critical systems or high compliance burden. | Cloud hosting provider, payroll vendor |
| 2 | Moderate | Vendors with limited data access or service impact; not business-critical. | Marketing automation tool |
| 3 | Low | Vendors with no access to sensitive systems or data; minimal operational risk. | Office supply vendor |
To determine a vendor’s tier, you can use a simple scoring model based on criteria like:
- Type of data accessed (e.g., PII, PHI, payment info)
- Level of system integration (e.g., admin vs. user vs. none)
- Operational dependency (how critical the service is to business continuity)
- Regulatory exposure (e.g., GDPR, HIPAA, PCI, etc.)
- Third-party or subcontractor use
Assign point values to each criterion and tally the results to place vendors into tiers. For example:
- Vendors scoring 80+ are Tier 1
- 50–79 fall into Tier 2
- Below 50 are Tier 3
You can adapt this framework based on your industry and internal risk appetite
Some organizations also introduce a Tier 0 or “Strategic” category for vendors that are deeply embedded in core strategy or customer-facing operations, even if their risk isn’t immediately apparent.
Pro Tip: Don’t make tiering a one-time event. Re-evaluate vendors annually or when major changes occur, such as new system integrations, data scope expansions or acquisitions.
8. Develop a Comprehensive Risk Management Plan for Vendors
A vendor risk management plan is your formal playbook for how your organization monitors, mitigates and responds to vendor-related risks over time.
Your plan should outline:
- The types of controls and assessments required for each vendor tier
- Timelines for reassessments, audits or documentation reviews
- Remediation processes if a vendor fails to meet your risk criteria
- Ongoing monitoring expectations (e.g., incident reporting, contract SLAs, risk score drops)
- Roles and responsibilities for internal stakeholders (Procurement, Legal, InfoSec, etc.)
A strong risk management plan should also include thresholds for escalating vendor issues, role-based access to risk dashboards and alerts for high-impact changes.
That kind of proactive monitoring is exactly what Jeff Kaiden, CEO of Capacity, emphasizes:
“We use a procurement platform that allows us to store vendor information and tag risk levels. If something changes, like a vendor gets acquired or starts missing deliveries, we can adjust their status. The system sends alerts to stakeholders so decisions can happen quickly. Dashboards help make the data easier to interpret, and we review the top risk vendors at least once a quarter.”
Rather than drafting this document from scratch, you can speed things up using Visme’s vendor risk plan templates. These are pre-designed, fully customizable documents built to help teams structure:
- Vendor risk policies
- Tier-based control matrices
- Escalation workflows
- Risk mitigation plans tied to specific vendor categories

With Visme’s AI document generator, you can also create a baseline risk management plan by simply describing your goals and vendor categories.
Once you choose the design, the AI will auto-generate a draft document, which you can refine with your team.
Our unified content creation tool makes it easier to:
- Maintain consistency across departments
- Quickly update policies as regulations or vendor relationships change
- Generate stakeholder-facing summaries or audit-ready documentation
And because Visme combines document design with data visualization, you can embed visual elements, such as tiered charts, decision matrices or control checklists, directly into your plan.

Incorporate interactive elements like popups and hover effects to make your plan engaging and easier for non-technical stakeholders to understand and act on. You can also repurpose it as a presentation, internal training asset, or compliance reference hub.
9. Perform Annual Assessments to Evaluate Vendor Risks
Annual assessments help you ensure that vendors are still meeting your standards, aligned with your risk appetite and safe to work with.
Your annual reassessment should cover the same core areas you reviewed during onboarding:
- Updates to security practices or policies
- Changes in data handling, hosting or system integrations
- New compliance certifications (or lapses in existing ones)
- Any reported incidents, breaches or control failures
- Financial or operational red flags
Use your previously completed questionnaire as a baseline. Ask vendors to confirm what has changed and supply updated documentation where necessary.
Also, tie your reassessment cycle to internal business reviews and consider the strategic importance of the vendor’s current role. If they’re now processing more sensitive data or supporting mission-critical functions, a deeper reassessment—even mid-cycle—may be warranted.
Keep close communication with vendor owners in IT, Legal, Procurement and business units so these shifts don’t go unnoticed.
Gianluca Ferruggia, General Manager of DesignRush, explains how a structured, cyclical approach helps teams stay proactive:
Pro Tip: Use shared dashboards to track reassessment dates, documentation status and outstanding follow-ups. Tools like Visme’s project tracker templates and dashboards help keep everything organized, visible to stakeholders and audit-ready.“Instead of using static reports, we record assessments in a secure digital system connected to vendor profiles, enabling dynamic updates as conditions change. Sharing is often done through controlled access within procurement and compliance departments, with senior leadership receiving simplified dashboards. The approach is cyclical, with planned reassessments timed in accordance with contract renewal intervals, ensuring our vendor risk profile remains current.”
10. Report on Your Vendor’s Performance
Once assessments are complete, the final step is to translate your findings into a clear, actionable report that helps internal stakeholders make informed decisions.

Your report should focus on:
- Vendor performance by tier
- Identified risks and control gaps
- Remediation status and follow-up actions
- Reassessment timelines and overdue reviews
- Trends in risk posture across your vendor ecosystem
Use this report to highlight where risk is increasing, which vendors require attention and how overall third-party risk is being managed over time.
To streamline your reporting process, Visme offers ready-to-use vendor risk assessment templates that help you present your findings clearly.

You can:
- Create structured reports that highlight vendor risks, controls and remediation plans
- Visualize vendor tiers, security ratings and control status through intuitive executive dashboards
- Embed interactive charts, graphs and data visualization to showcase key metrics and KPIs
- Summarize key takeaways in a concise board report for review and decision-making
- Build an interactive board presentation to highlight areas of concern and outline next steps for risk mitigation
Racing against the clock? Let our AI report generator do the heavy lifting. Just describe your assessment results and risk areas and the tool will instantly generate a structured report, plan, checklist or any type of document you need.
Next, select your preferred design theme; the AI tool will generate a structured document that you can customize, brand and share.
With our brand wizard, you can instantly apply your company’s fonts, colors and logo to ensure every report is professionally branded and presentation-ready in minutes.
Once finalized, export your report in PDF, HTML or presentation format or embed it into internal dashboards for easy access across teams.
Risk Scoring Matrix: How to Prioritize What Matters
Not all risks are created equal. That’s why, once you've completed your vendor assessment, the next step is to assign risk levels to each issue you uncover so your team knows where to focus resources first.
On a supplier risk assessment matrix, Likelihood and Impact are the two primary dimensions. Together, they form a heat map that helps you visually prioritize which vendor risks need attention.
The 4x4 matrix shown below is the simplest form of a vendor risk scoring matrix.
Made with Visme Infographic Maker
Each risk is scored on two scales:
- Likelihood: How likely is the risk to occur? (Y-axis)
- Impact: How damaging would it be to your business if it did? (X-axis)
Each cell shows the number of vendors with a particular combination of likelihood and impact.
Colors represent severity across 4 levels of risk:
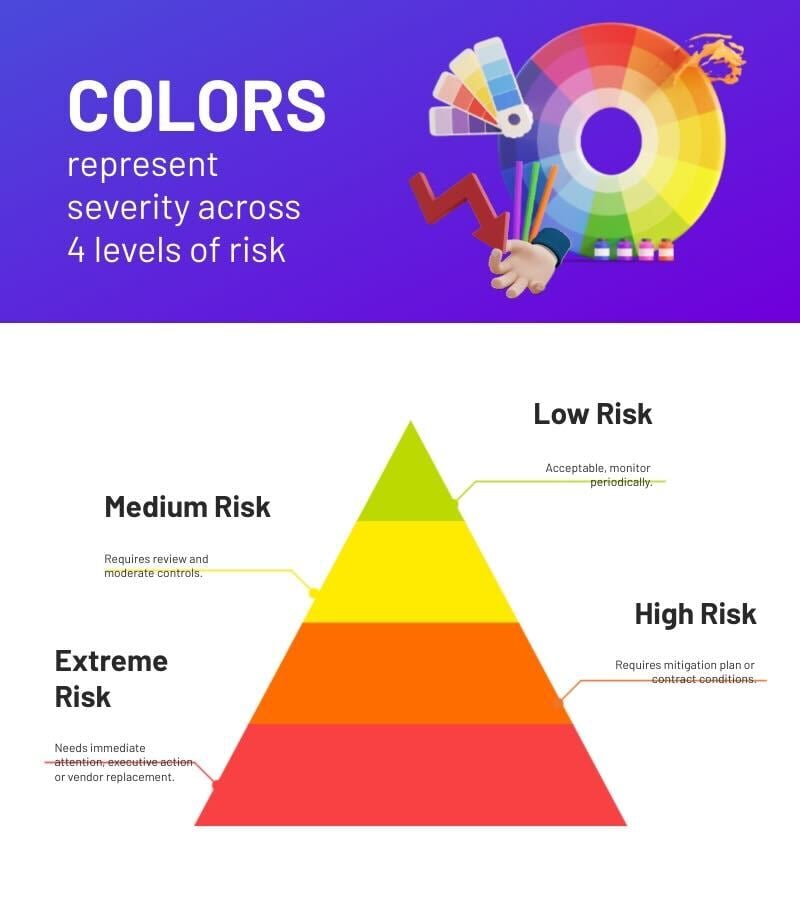
If your cybersecurity program is more advanced, you’ll benefit from a more sophisticated risk matrix. It should match the level of detail in your severity ratings and compliance requirements.
This means you can opt for an advanced 8x8 grid, as shown below, or use the 10x10 matrix.
Made with Visme Infographic Maker
In this 10×10 risk matrix below, Likelihood is rated from 1 (rare) to 10 (certain). Impact is rated from 1 (negligible) to 10 (catastrophic).
Made with Visme Infographic Maker
Let’s walk you through a few scenarios to help you make sense of this grid.
Made with Visme Infographic Maker
Real Examples of Vendor Risks
To show how vendor risk can unfold in the real world, here are notable examples where breaches and compliance failures by third parties have led to serious consequences.
Slack: Internal Process Risk & Credential Exposure
In July 2022, Slack revealed a bug in its shared invite link feature that had been around for five years. This bug affected users who created or revoked shared invite links between April 17, 2017, and July 17, 2022, by sending hashed versions of their passwords to other members in the workspace. Once they found out about the issue, Slack reset the passwords of those affected.
To address this, Slack created a new system to spot and block exposed passwords and session cookies. They used threat intelligence feeds to check for compromised credentials and can revoke them automatically, often before any attackers can exploit them. Users receive real-time alerts, and for enterprise customers, logs are maintained for transparency and compliance.
What's key here is understanding the type of risk this poses. It wasn't a failure in Slack's overall security. Rather, it was a slip-up in how they managed credentials. Even hashed passwords can be cracked if vendors don’t keep an eye on their use or misuse.
Key Takeaway: Mistakes within a company can be just as risky as external attacks. If your business relies on tools like Slack for messaging and collaboration, this incident highlights the importance of knowing where your data is going. It also shows the importance of understanding how external platforms manage user credentials and authentication behind the scenes.
Zoom: Misleading Encryption Claims & Third-Party Scrutiny
In 2020, Zoom claimed to offer end-to-end encryption (E2EE). But investigations revealed that Zoom actually used Transport Layer Security (TLS), meaning the data was only encrypted between the user and Zoom’s servers, not between users. In theory, this would create a scenario where the service could access user data at its discretion and leave the door wide open for potential eavesdropping by determined third parties.
This misrepresentation triggered lawsuits. One of the lawsuits alleged violations of the District’s Consumer Protection Procedures Act, with penalties up to $1,500 per user affected. The advocate noted that Zoom “lulled consumers and businesses into a false sense of security, especially in healthcare, where data privacy is paramount.
In response, Zoom acquired Keybase to rebuild its encryption infrastructure from the ground up. It published detailed technical plans, began beta-testing real end-to-end encryption (E2EE) for all users and committed to stronger data protection.
Key Takeaway: This scenario exemplifies a vendor transparency risk. If a vendor’s claims are inaccurate or overstated, it introduces legal, compliance and reputational exposure for your business. Ensure that you verify claims related to encryption, data routing and regulatory compliance, particularly for mission-critical tools. Audit both the technology and the legal language in vendor agreements to prevent exposure from inaccurate security assurances.
Target: HVAC Vendor Breach Exposes Millions
In 2013, retail giant Target suffered one of the most infamous vendor-related data breaches in history.
Hackers infiltrated Target’s network by stealing credentials from a third-party HVAC vendor. These credentials gave attackers access to Target’s internal systems, where they deployed malware that harvested sensitive customer information. They accessed sensitive data, including full names, emails, credit card numbers, verification codes and more. The breach compromised the payment data of 40 million customers and the personal details of another 70 million, affecting over 110 million individuals.
This incident is a textbook case of third-party access risk. Pair vendor monitoring with cloud detection and response to detect lateral movement, correlate IAM and workload signals across accounts, and automate targeted containment when suspicious cross-account activity appears.
While the HVAC vendor didn’t handle customer data directly, its remote access privileges created a pathway into Target’s core systems. Poor network segmentation and a lack of robust vendor access controls allowed attackers to escalate privileges and reach the customer service database. In total, Target incurred $236 million in damages, including $18.5 million in multi-state settlements and more than 140 lawsuits.
Key Takeaway: Any third party with network access—no matter how “non-technical” their role seems—can become a high-risk point of entry. Businesses must apply the principle of least privilege, implement strong segmentation and regularly audit vendor access to prevent similar supply chain attacks.
Vendor Risk Assessments FAQs
A complete risk assessment, especially when evaluating vendors, should cover:
- Asset Identification: Identify the specific data, systems or services that are impacted by the vendor relationship.
- Threats & Vulnerabilities: Identify potential risks, such as cyberattacks, regulatory violations, service disruptions or financial instability.
- Likelihood and Impact Analysis: Estimate how likely each risk is to occur and how severely it would affect your operations.
- Risk Prioritization: Assign a score or level (low, medium, high) to help focus resources on the most critical risks.
- Mitigation Measures: Document how you’ll reduce or manage each risk, whether that’s through technical safeguards, contract terms or third-party audits.
Vendor risk is typically calculated using a weighted scoring system. Here’s a simplified version:
1. Define key risk categories applicable to your organization
2. Score each vendor: Rate the vendor in each category on a consistent scale (e.g., 1 to 5, where 5 is high risk).
3. Apply category weights: Weight each category based on its importance to your organization.
4. Calculate the weighted score: Multiply the score in each category by its weight and add them together to get a total vendor risk score.
5. Classify the risk: Based on the score, categorize vendors as low, medium or high risk so you know where to dig deeper or apply extra controls.
At a minimum, a robust vendor risk assessment should include:
- Due diligence: Gather company info, financials, services provided and data access levels.
- Security & compliance questionnaire: Send out a standardized form covering topics like encryption, access controls, incident response and certifications (e.g., SOC 2, ISO 27001).
- Evidence of controls: Request proof, such as audit reports, security ratings, or policy documents.
- Risk tiering model: Place vendors into risk categories (critical, high, medium, low) based on their impact on your business and risk profile.
- Contractual and operational safeguards: Your vendor contracts should include key protections such as breach notification requirements, service-level agreements (SLAs), rights to review processes or data and termination clauses.
How Visme Helps With Vendor Risk Communication
When it comes to vendor risk, spotting threats is only half the job.
You need to communicate them clearly, quickly and in a way that prompts real action. That’s where Visme becomes a strategic asset.
Visme helps you turn complex vendor risk data into clean, professional reports and dashboards that your stakeholders can easily interpret and act on. Access a wide range of templates, features, design assets and AI tools that empower you to:
- Visualize vendor tiers, performance and risk trends with customizable charts
- Generate AI-powered reports directly from your assessment findings
- Build interactive dashboards that keep teams aligned in real time
- Develop security and vendor risk assessment questionnaires to collect data with branded, interactive forms
- Standardize your communications with branded templates for assessments, follow-ups and annual reviews
Create an account or book a demo to see how Visme can streamline your entire vendor risk management process
Create Stunning Content!
Design visual brand experiences for your business whether you are a seasoned designer or a total novice.
Try Visme for free