What Is Soar? A Detailed Guide to Platforms + Templates

Every 39 seconds, a cyberattack takes place.
That’s 2,200 attacks per day, each one with the potential to cost businesses millions.
In the U.S. alone, the average data breach comes with a staggering $9.44 million price tag. With cybercrime predicted to reach a mind-blowing $8 trillion in global costs, it’s clear that the stakes have never been higher.
The challenge for security teams isn’t just the sheer volume of threats but the speed and precision required to respond effectively.
This is where SOAR—Security Orchestration, Automation and Response—steps in to help security teams automate repetitive tasks and respond to incidents faster and smarter.
So, what is SOAR and how does it elevate your organization’s security architecture? Keep reading to find out how SOAR works, its benefits and challenges, the different use cases and the best SOAR platforms and vendors available in the market.
Let’s dive in.
Table of Contents
- What is SOAR?
- Benefits of SOAR
- Challenges of SOAR
- SOAR Use Cases
- Templates for Implementing SOAR Best Practices
- 6 Best SOAR Platforms & Vendors
- SOAR FAQs
Quick Read
- SOAR which stands for Security Orchestration, Automation and Response refers to a set of tools that streamline security operations by integrating tools, automating tasks and improving response to threats.
- SOAR platforms help teams detect and respond to threats faster, improve collaboration across the board and scale up your security as you grow.
- The challenges of SOAR include integration with existing tools, complexity of setup, cost of implementation, need for skilled personnel and maintaining accuracy.
- SOAR excels in automating incident response, threat hunting, phishing management, vulnerability handling, compliance reporting, integrating threat intelligence, alert triage, insider threat detection, orchestrating across tools and enhancing behavior analytics for a streamlined and efficient security strategy.
- The leading SOAR platforms include Palo Alto Networks, Cortex XSOAR, Splunk Phantom, Cyware, IBM Security QRa2dar SOAR, Microsoft Sentinel and Swimlane.
- Pairing your SOAR platform with Visme gives your team the visual resources needed to streamline processes, from creating SOPs, playbooks to mapping workflows with flowcharts and engaging presentations.
- Create an account with Visme to simplify complex security strategies into accessible, branded materials that empower your team to respond effectively and consistently.
What is SOAR?
SOAR—Security Orchestration, Automation and Response—is a suite of tools or processes designed to improve the efficiency of your security operations by automating routine tasks, coordinating responses to threats and simplifying workflows.
According to Gartner, which first coined the term "SOAR" in 2015, “SOAR solutions combine incident response, orchestration and automation and threat intelligence (TI) management capabilities in a single platform. They are also used to document and implement processes (aka playbooks, workflows and processes); support security incident management, and apply machine-based assistance to human security analysts and operators.”
SOAR platforms provide security operations center (SOC) teams with a central console to integrate tools, optimize threat response workflows and manage all security alerts in one place.
This centralized approach eliminates the need for manual, time-consuming tasks and lets SOC teams automate repetitive low-level processes and laser focus on critical issues. The result is increased productivity and a stronger, more proactive security posture for the organization.
How Does SOAR Work?
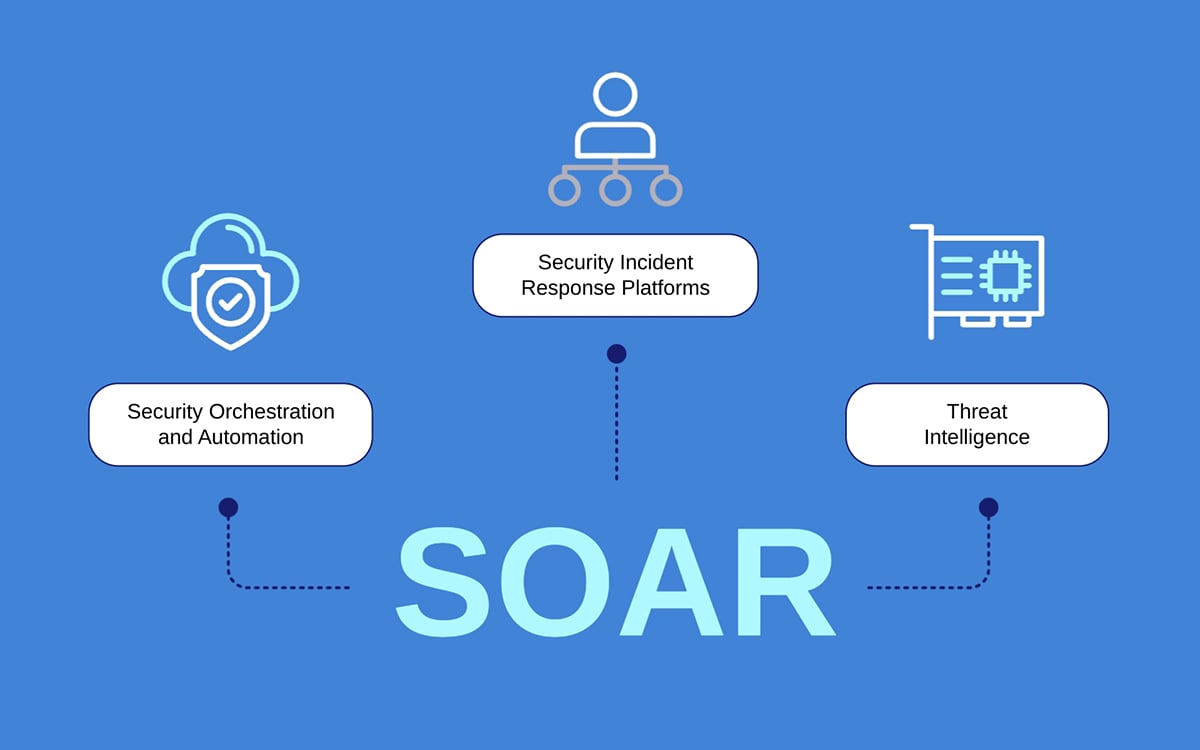
To help you understand how SOAR solutions work, here’s a breakdown of its three major components:
Security Orchestration
Security orchestration lets IT and cybersecurity teams connect various security tools and systems so that information is shared and centralized to make incident response faster and more effective.
For example, an organization uses multiple threat detection tools: an intrusion detection system (IDS), endpoint detection and response (EDR) and a firewall. Instead of manually collecting data from each tool, a SOAR solution automatically gathers alerts from all of them, correlates the information and triggers an appropriate action, such as blocking an IP address on the firewall.
Security Automation
The automation capability is what sets SOAR solutions apart from other security systems. SOAR solutions automate repetitive tasks that would normally require deploying multiple tools, such as log analysis, threat detection and incident response. This reduces the workload on security analysts and improves response times.
For example, if a phishing email is detected, the SOAR system can automatically trigger a workflow that removes the email from all inboxes, blocks the sender and generates a report. This eliminates the need for manual intervention in every incident but much more than that, allows security teams to focus on higher-level decision-making.
Threat Response
With SOAR, organizations can plan, manage and coordinate their actions to quickly deal with security incidents. When a potential threat is detected, SOAR solutions trigger guided responses or automated playbooks to handle specific types of incidents, such as malware infections, phishing attempts, or unauthorized access.
For a malware detection incident, the SOAR platform might execute a predefined playbook that includes isolating the affected system, conducting a forensic analysis and restoring the system from a clean backup. Analysts can monitor the process and intervene if necessary.
Before automated playbooks are implemented, they need to be carefully planned and documented. Visme comes packed with customizable templates that help security teams create visually engaging and easy-to-understand flowcharts, decision trees and diagrams that show each step in the response process.
Made with Visme Presentation Maker
SOAR vs SIEM vs XDR: What’s the Difference?
| Feature | SOAR (Security Orchestration, Automation and Response) | SIEM (Security Information and Event Management) | XDR (Extended Detection and Response) |
| Primary Purpose | Automates and coordinates security operations and incident response. | Collects, analyzes and correlates security data for threat detection. | Provides a unified view of security data across endpoints, networks and cloud environments for detection and response. |
| Key Functionality | - Automates tasks and workflows - Orchestrates incident response - Reduces manual intervention |
- Collects data from various sources - Analyzes logs and events for potential threats - Generates alerts |
- Detects threats across various security layers - Correlates data from multiple sources - Provides automated response actions |
| Response Capabilities | Automates response actions with playbooks. | Generates alerts, no direct response. | Automates responses to detected threats. |
| Integration | Integrates with various security tools (e.g., SIEM, firewalls, EDR) for automation and response. | Integrates with log sources, network devices, endpoints and cloud for data collection and analysis. | Integrates deeply with endpoints, networks and cloud services for broader detection and response coverage. |
| Automation | High: Automates repetitive tasks and response workflows. | Low: Focuses on detection and alerting, but no automation of responses. | Moderate: Automates responses to certain detected threats. |
Benefits of SOAR
Here are some of the top benefits of using a SOAR system.
Faster, Smarter Response to Threats
Cyber threats are getting bigger and more complex. New types of attacks mean that companies have to implement new ways to fight them. Sometimes, this means hiring more people or buying more tools to keep up.
But with SOAR, much of this work can be automated. It takes care of repetitive tasks like sorting through alerts and checking logs, allowing security teams to focus on higher-priority issues. By automating many tasks, SOAR helps teams detect and respond to threats faster, saving both time and energy while making the whole process more efficient.
Meeting Budgetary Needs
As the number and types of cyber threats grow, businesses face bigger budget problems. Each new threat often may require hiring more people and buying extra tools or software.
But with SOAR, many of these steps are automated and simplified. It handles tasks like collecting data and responding to threats automatically. This helps save money on hiring more staff and buying more equipment, allowing companies to stay within budget while still keeping their security strong.
Reliable and Consistent Action
When different people handle the same threat in different ways, it can lead to confusion. Without clear steps to follow, mistakes can happen. SOAR makes sure that all threats are handled the same way every time. It uses playbooks that guide the team through each step of the process, so nothing gets missed and the response is always reliable.
Better Teamwork Across the Board
Big companies have different teams responsible for various security aspects. Working in silos can create communication issues and slow down the response to a threat. SOAR makes it easier for teams to work together by bringing all the information into one place.
In addition to the SOAR, it’s also important to create documentation and SOPs to keep team members on the same page regarding security protocols.
Tap into Visme’s template library to create standard operating procedures (SOPs), training materials, infographics, videos and presentations that help you explain how the SOAR system operates, how playbooks are triggered and what team members need to do during an incident.
Challenges of SOAR
While SOAR offers several benefits, below are various challenges of using a SOAR system:
Integration with Existing Tools
One of the biggest challenges with SOAR is getting it to work smoothly with all the other security tools a company already uses. Many businesses rely on different systems for things like monitoring, alerting and responding to threats.
Connecting SOAR to these tools can be tricky, especially if the systems don’t integrate well. It takes time and effort to make sure everything works as one and sometimes, it may require extra technical expertise.
Complexity of Setup
SOAR solutions can be complex to set up, especially for organizations that don’t have a lot of experience with automation or orchestration. The initial setup can be time-consuming and require a lot of planning. Defining the right playbooks, deciding which tasks should be automated and setting up workflows all require experience, expertise and testing.
Customizing for Specific Needs
Every organization faces different types of threats and has its own way of responding to them. SOAR platforms need to be customized with detailed workflows and playbooks that match those specific needs. For companies with unique security challenges or highly specific requirements, this can be time-consuming and may not always meet every requirement.
Cost of Implementation
SOAR solutions can be expensive to implement, especially for smaller companies or those with limited budgets. The cost includes not just the software but also the time spent on training, integration and customization. Some companies may struggle to justify SOAR’s upfront cost due to delayed savings, making it a tough budget decision.
Need for Skilled Personnel
Although SOAR helps automate many tasks, it still requires skilled professionals to set it up and maintain it. Security analysts need to understand the platform well enough to create effective playbooks, respond to complex incidents and tweak the system as needed.
Without the right expertise, the platform might not perform as expected, which can limit its effectiveness. Hence, the need for effective training and onboarding of new members of the Security Operations Center (SOC).
Over-Reliance on Automation
While automation is one of the key benefits of SOAR, it can also be a drawback if it’s overused. Too much automation might lead to complacency, where teams rely too heavily on the system and fail to notice potential gaps in the response process. There’s a risk of ignoring the human judgment needed to handle more complex or nuanced threats. Striking the right balance between automation and human oversight is critical for SOAR to be effective.
Maintaining Accuracy
As SOAR platforms automate responses, it’s important to ensure that they’re accurate and not causing unintended consequences. For example, blocking an IP address or quarantining a system based on an automated rule might accidentally disrupt legitimate business operations. Regular review and fine-tuning are needed to keep everything running smoothly and avoid false positives that could slow down the business.
SOAR Use Cases
Made with Visme Infographic Maker
SOAR isn’t just another security tool—it’s a complete solution that helps solve a wide variety of security problems faster and more efficiently.
Here are 10 use cases where SOAR outperforms any other security operations tool in your arsenal.
1. Automated Incident Response
SOAR helps automate routine responses to common security incidents like phishing, malware infections and unauthorized access. When an alert is triggered, SOAR can automatically initiate predefined actions, such as isolating affected devices, blocking IP addresses or notifying key personnel.
2. Threat Hunting and Investigation
SOAR platforms collect and correlate data from various sources, making it easier for analysts to perform threat hunting. By automating data gathering and enriching alerts with context, SOAR enables faster and more thorough investigations of suspicious activities.
3. Phishing Attack Management
Phishing attacks generate a high volume of alerts that can be overwhelming for security teams. SOAR can automate the analysis of suspicious emails by extracting URLs and attachments, running them through threat intelligence systems and quarantining harmful messages.
4. Vulnerability Management
SOAR integrates with vulnerability scanners and patch management tools to automate the process of identifying, prioritizing and remediating vulnerabilities. It helps security teams focus on the most critical risks by streamlining workflows and reducing manual effort.
5. Compliance Reporting
SOAR can automatically generate reports on incidents and responses to help organizations meet regulatory requirements. This system makes audits less time-consuming and enables SOCs to comply with standards like GDPR, HIPAA and PCI-DSS.
6. Threat Intelligence Integration
By integrating threat intelligence feeds, SOAR platforms can enrich alerts with relevant data, such as known malicious IPs or domains. This improves decision-making and speeds up the process of determining whether an alert represents a real threat.
7. Alert Triage and Prioritization
SOAR reduces alert fatigue by automating the triage process. It can prioritize alerts based on severity, context and past incidents so that analysts focus on the most critical threats first.
8. Insider Threat Detection
SOAR helps detect and respond to insider threats by integrating with user behavior analytics (UBA) and identity management systems. When suspicious user activity is detected, SOAR can trigger actions such as locking accounts or escalating the incident for investigation.
9. Security Orchestration Across Multiple Tools
Many organizations use multiple security tools that don’t always work together. SOAR acts as a central hub, orchestrating workflows across various systems—like SIEM, firewalls, endpoint detection and response (EDR) and more—ensuring a coordinated defense strategy.
10. User and Entity Behavior Analytics (UEBA) Integration
SOAR platforms can work alongside UEBA systems to detect and respond to insider threats and unusual behavior patterns. When UEBA detects anomalies—like unusual login times or large file transfers—SOAR can automatically trigger a response, such as locking the user account or escalating the incident to security analysts.
Templates for Implementing SOAR Best Practices
When it comes to SOAR, having the right documents in place is key. Instead of starting from scratch, save time and streamline your workflow with these ready-to-use templates—designed to keep your processes efficient and organized. Here are a few listed below:
SOAR Analysis Presentation Template
This presentation layout includes everything you need, such as incident details, impact assessment, automation investigation, threat intelligence, automated actions, timelines, and post-incident reviews. It’s perfect for sharing incidents with key stakeholders who require quarterly and annual reviews.
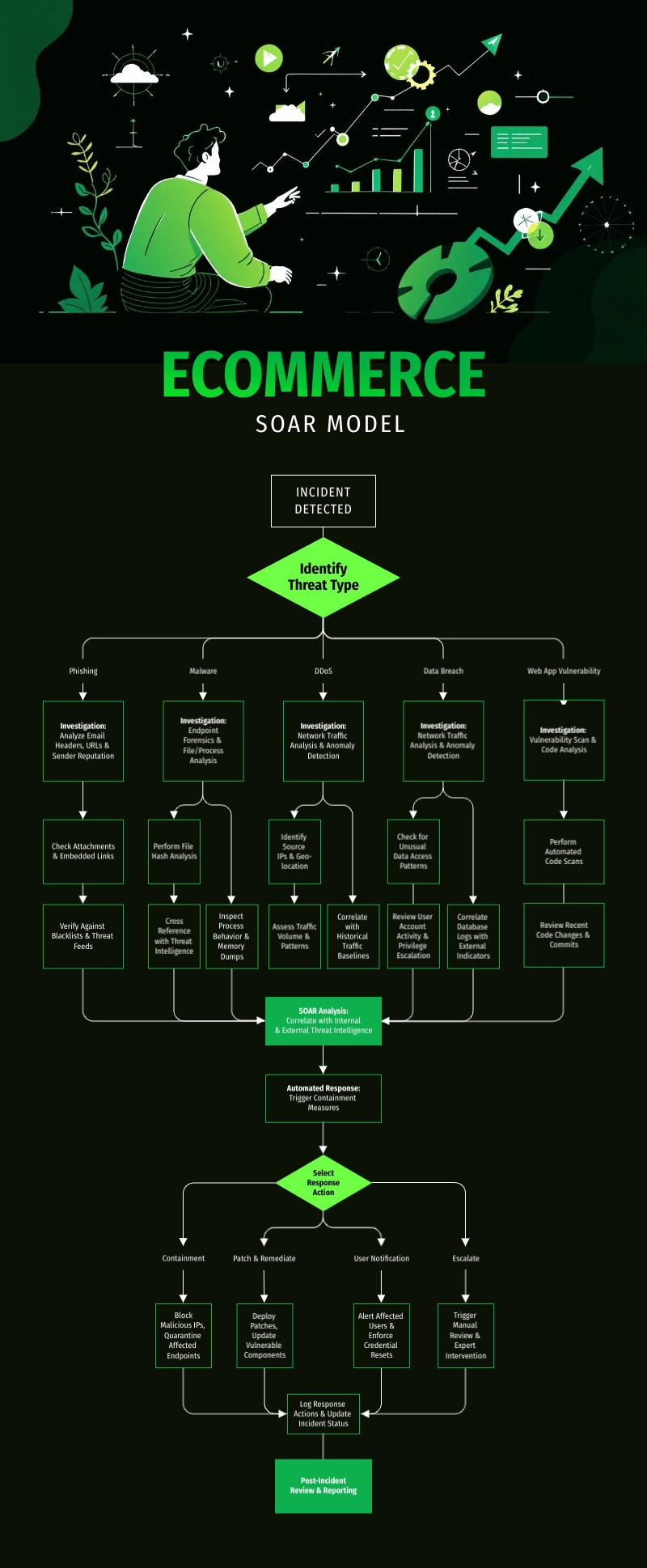
SOAR Model Infographic Template
If you need a clear, professional way to present your SOAR model insights, this infographic template is a great place to start. Designed for security teams, analysts, and IT professionals, it breaks down key areas like incident details, all in an easy-to-digest format.
With its smart use of structured sections, intuitive flow, and visually engaging elements, this template helps you communicate critical security insights effectively. You can customize colors, layouts, and icons to match your brand.
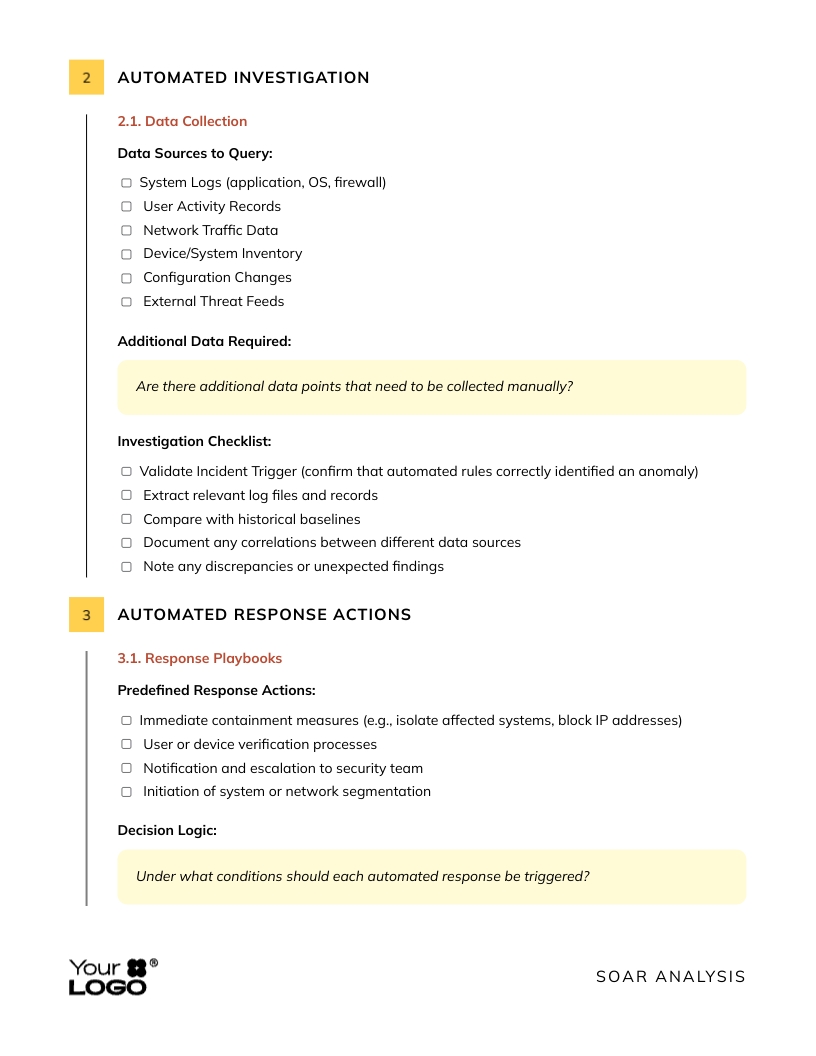
SOAR Analysis Worksheet Template
Let’s say you want a worksheet that teammates can easily use to fill out incident reports—whether digitally or by hand. This template is a great option. All the details are laid out across two pages with a spacious, clean design that makes it easy to read and fill out.
You can quickly rebrand it with your company’s colors and logo and modify sections to align with your security measures and specific details. You can use this or discover more SOAR templates that Visme provides.
6 Best SOAR Platforms & Vendors
In this section, I’ve reviewed the leading SOAR vendors and solutions in the market. But before I get to it, let’s explain what SOAR products are.
What are SOAR Products?
SOAR (Security orchestration, automation and response) products bring together incident response, automation, orchestration and threat intelligence (TI) management into one platform.
These tools also help document and implement key processes, such as playbooks and workflows, support incident handling and provide machine-powered assistance to security analysts and teams.
Let’s review a list of 10 tools that check these boxes.
| Tool | Best for | Features | Pricing | Rating |
| Splunk SOAR | Large organizations with mature security operations looking for advanced automation and orchestration. | Automated playbooks, 300+ third-party tool integrations, case management | Custom pricing based on workload, entity, or ingest. Requires estimate. | Gartner: 4.2/5 G2: 4.3/5 |
| Cortex XSOAR | Enterprises needing a SOAR solution with strong collaboration and automation features. | 900+ prebuilt integrations, visual playbook editor, threat intel integration, virtual war room for collaboration | Custom pricing. Requires demo. | Gartner: 4.6/5 G2: 4.5/5 |
| IBM QRadar SOAR | Organizations with strict compliance requirements and those already using IBM’s security tools. | Automated workflows, real-time collaboration, breach response with 200+ regulations, 300+ tool integrations | Custom pricing based on program scale. Requires demo. | Gartner: 4.3/5 G2: 4.1/5 |
| FortiSOAR | Large enterprises and MSSPs, particularly those already using Fortinet solutions. | 500+ integrations, AI-driven security operations, prebuilt workflows, threat intelligence from FortiGuard Labs | Custom pricing. Free demo available. | Gartner: 4.9/5 G2: 5.0/5 |
| Swimlane Turbine | Teams of all sizes, especially those without dedicated development resources. | No/low-code playbook builder, AI-driven Python scripting, advanced dashboards, handles millions of alerts daily | Enterprise and MSSP pricing tiers. Contact sales for details. | Gartner: 4.8/5 G2: 4.6/5 |
| Microsoft Sentinel | Teams needing a cloud-native SIEM and SOAR solution with powerful AI-driven threat detection capabilities. | Scalable data collection, Advanced threat detection, interactive investigations, proactive threat hunting | Pricing based on data analyzed and stored in Azure Monitor. Visit pricing page for details. | Gartner: 4.3/5 G2: 4.4/5 |
1. Splunk SOAR

Best For: Large organizations with mature security operations looking for advanced automation and orchestration.
Splunk SOAR is designed to make security teams work smarter, not harder. It connects with over 300 third-party tools and automates tasks, so you don’t have to completely redo your existing security setup.
When you combine it with Splunk Enterprise Security, it gives you a seamless experience for managing and responding to threats. Thanks to its data-driven approach and machine learning, Splunk SOAR helps organize, prioritize and act on alerts quickly, which means your team can focus on what matters most—staying ahead of security risks.
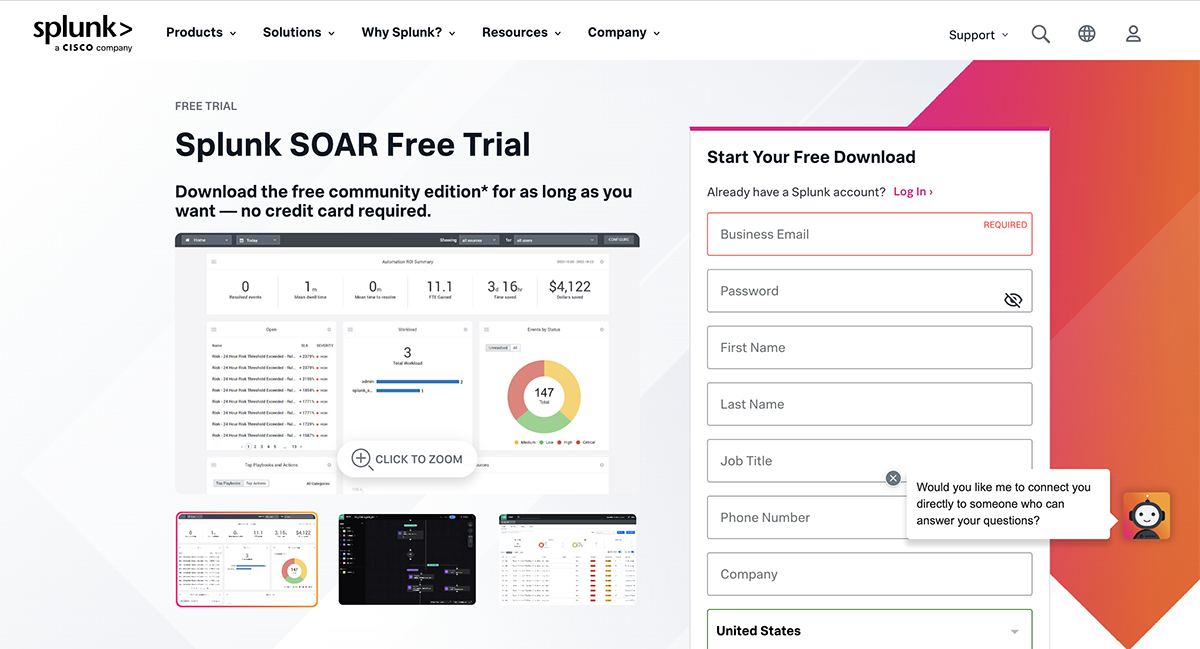
The best part? Splunk SOAR comes with customizable playbooks that help you automate everything from simple tasks to more complex workflows.
It even has prebuilt playbooks based on the MITRE ATT&CK and D3FEND frameworks, so you can hit the ground running. Whether you go for a cloud, on-premises or hybrid setup, it integrates smoothly with your existing tools and makes security automation easy, no matter your experience level.
Features
- Automated Playbooks: Execute actions across security and IT tools in seconds instead of hours with prebuilt and customizable playbooks.
- App Integration: Integrates with 300+ third-party tools and supports 2,800+ automated actions for coordinating complex workflows.
- Simple, Scalable Security Automation: The Visual Playbook Editor makes it easy to create custom workflows, regardless of coding experience.
- Comprehensive Case Management: Facilitates task segmentation, assignment and documentation to ensure a collaborative investigative process.
- Infused with Intelligence: Helps prioritize threats using a centralized investigation panel and insights from the Splunk Threat Research Team.
- Flexible Deployment Options: Available in cloud, on-premises or hybrid environments and integrates seamlessly with Splunk Enterprise Security.
Pricing
Splunk has three pricing options: Workload, Entity and Ingest. You’ll need an estimate to find the best plan for your needs.
Ratings
- Gartner Peer Insights: 4.2/5 (81 reviews)
- G2: 4.3/5 (415 reviews)
- Capterra: 4.6/5 (242 reviews)
2. Cortex XSOAR

Best For: Enterprises needing a SOAR solution with strong collaboration and automation features.
Cortex XSOAR is built to take the hassle out of your security operations by automating repetitive tasks, so your team can focus on what really matters—strengthening your security posture.
With over 900 prebuilt integrations and automation packs, setting up and scaling security workflows becomes a walk in the park. It offers a wide variety of automation content packs across different use cases, so you can hit the ground running and get your systems up and running faster.
Plus, with the ability to orchestrate across your entire SOC, Cortex XSOAR pulls people, processes and technology together for a truly unified approach to incident response.
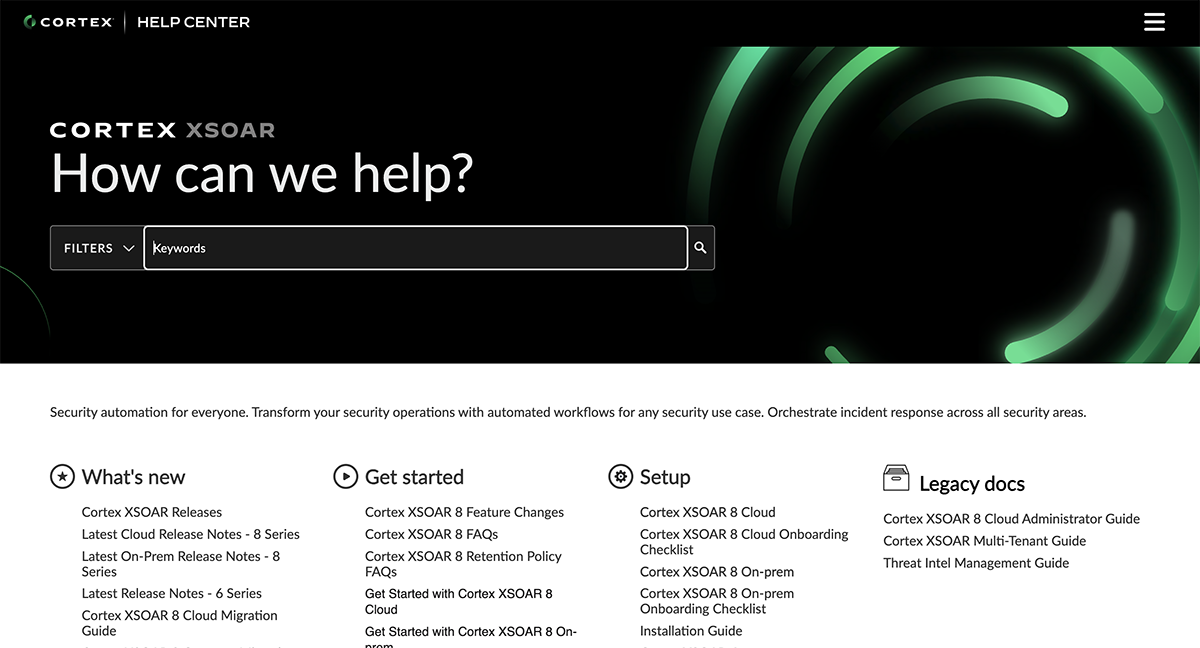
Another standout feature of Cortex XSOAR is its ability to speed up investigations. All incident data, threat intel and indicators are fully integrated into one platform, meaning everything you need to respond to and resolve an incident is right at your fingertips.
The platform also features a virtual war room, where teams can collaborate in real-time, track progress and manage tickets efficiently. After an incident, Cortex XSOAR also provides post-incident analysis and reporting so your team can learn from each event and continuously improve.
Features
- Automated Workflows: Automate repetitive tasks with 900+ integrations and create custom workflows using the visual playbook editor—no coding required.
- Fast Incident Investigation: Collaborate in real-time with a virtual war room, plus ChatOps and CLI for quick, on-the-spot actions.
- Top-Notch Threat Intelligence: Get high-quality threat intel from Unit 42™ to process indicators and update EDLs automatically.
- Seamless Integration: Integrate Cortex XSOAR with Palo Alto Networks products and third-party tools for a smooth, unified experience.
- Centralized Incident Response: Orchestrate and manage incident response across your teams and tools, making the process faster and more efficient.
Pricing
Cortex XSOAR doesn’t provide upfront pricing, you’ll have to request a demo to explore how it can support your SOC.
Ratings
Gartner Peer Insights: 4.6/5 (64 reviews)
G2: 4.5/5 (18 reviews)
Capterra: 5.0/5 (3 reviews)
3. IBM QRadar SOAR(formerly Resilient)

Best For: Organizations with strict compliance requirements and those already using IBM’s security tools.
When responding to a security incident or cyberattack, the decisions you make in the first moments are crucial. But too many teams still rely on manual processes or custom code without full automation. QRadar SOAR solves that by optimizing your team’s decision-making, automating repetitive tasks, and improving the overall efficiency of your Security Operations Center (SOC).
The cherry on top is QRadar SOAR's dynamic playbooks, which help cut response times by automating workflows and providing recommended actions. Plus, it’s got an award-winning interface that’s as easy to use as it is powerful.
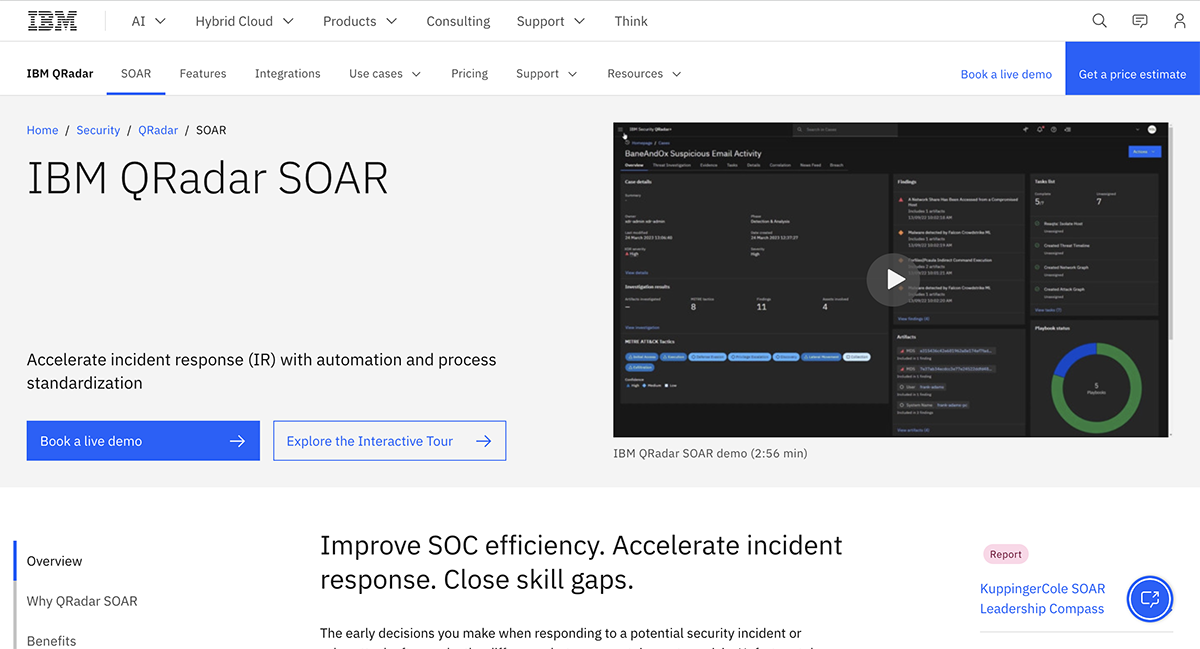
QRadar SOAR is also designed to streamline incident response across different teams and tools, with over 300 integrations and even helps manage compliance with over 200 privacy and data breach regulations. Whether you’re dealing with a security breach or responding to a threat, QRadar SOAR keeps everything organized and moving quickly.
Features
- Automated Workflows: Automate repetitive tasks and create custom workflows in minutes using the visual playbook editor—no coding skills needed.
- Fast Incident Investigation: Speed up your incident response with real-time collaboration in a virtual war room, plus ChatOps and CLI for quick actions.
- Breach Response: Simplify compliance with over 200 international data breach regulations, automating privacy reporting tasks and ensuring your response aligns with laws.
- Integrations and SOAR Apps: Connect seamlessly with over 300 integrations to streamline your incident response and orchestration processes.
- Analytics Dashboard: Visualize and track incident progress with a customizable analytics dashboard, helping your team stay organized and informed.
Pricing
QRadar SOAR offers a pricing plan that scales with your program. Book a live demo to get information or get a price estimate.
Ratings
- Gartner Peer Insights: 4.3/5 (11 reviews)
- G2: 4.1/5 (30 reviews)
- Capterra: 4.5/5 (33 reviews)
4. FortiSOAR by Fortinet

Best For: Large enterprises and MSSPs, particularly those already using Fortinet solutions.
For security teams eager to step away from the chaos of managing multiple tools, endless alerts and manual tasks, FortiSOAR is the perfect match.
By centralizing incident management and automating those repetitive, time-consuming activities, FortiSOAR helps you focus on what truly matters—stopping threats before they escalate. It serves your command center, where workflows are streamlined and responses are automated so your analysts can stay sharp and ahead with a data breach alert.
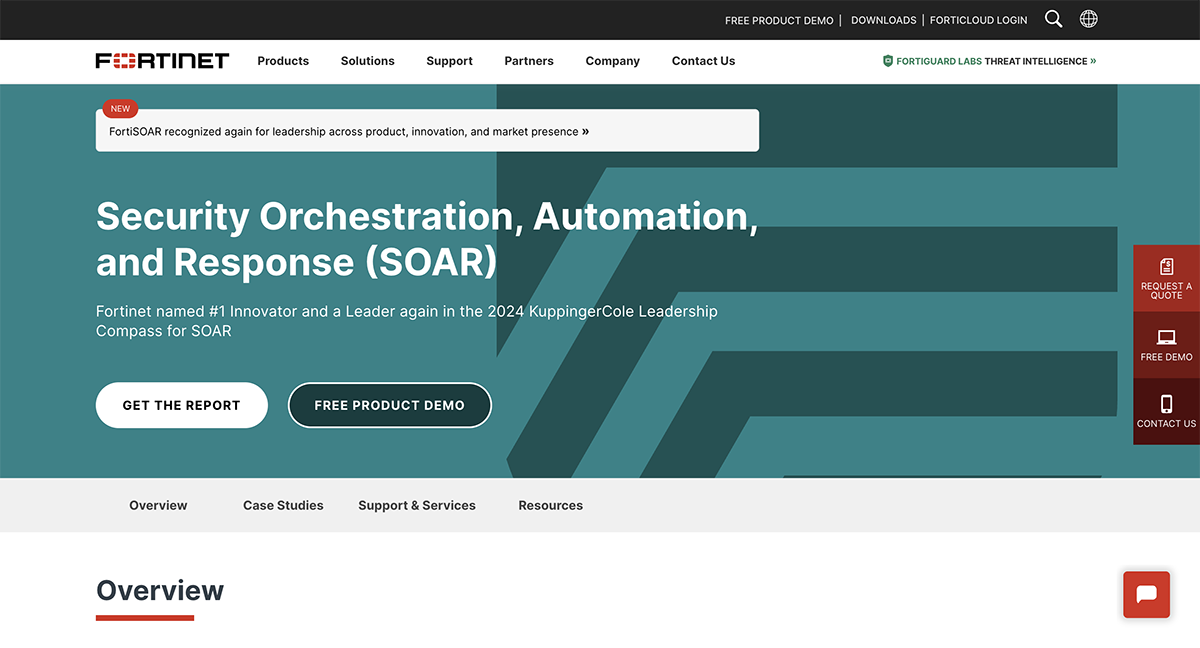
FortiSOAR shines in its ability to integrate seamlessly with over 500 tools and scale efficiently across diverse environments, including cloud and on-premises setups.
It’s packed with pre-built workflows that are ready to go and you can easily create custom ones without writing a single line of code. With FortiSOAR, you get an AI-driven security operations platform that not only supports IT and OT security but also ensures your response processes are more efficient and smarter.
Features
- Automated Workflows: Automate repetitive tasks with 500+ integrations and create custom workflows using the visual playbook editor—no coding required.
- Fast Incident Investigation: Collaborate in real-time with dashboards and automated case reporting while the visual playbook editor accelerates response times.
- AI-Driven Security Operations: Use FortiAI to guide your team with recommendations and automated tasks, streamline workflows and boost decision-making speed.
- Built-In Threat Intelligence: Tap into FortiGuard Labs' global intelligence to enrich investigations and power automated actions across your network.
- Content Hub & Community: Access a treasure trove of connectors, playbooks and solution packs, all while learning from a community of security experts.
- No/Low-Code Playbook Creation: Build custom playbooks quickly without coding knowledge using FortiSOAR’s drag-and-drop interface
- Flexible Deployment Options: Choose between SaaS, on-premises or cloud-hosted options to match your business needs.
Pricing
FortiSOAR offers a free product demo. Contact sales to request a custom quote for your needs.
Rating
- Gartner Peer Insights: 4.9/5 (115 reviews)
- G2: 5.0/5 (3 reviews)
- Capterra: No reviews at the moment
5. Swimlane Turbine

Best For: Teams of all sizes, especially those without dedicated development resources.
Swimlane Turbine is a game-changer for modern security operations as it combines automation, generative AI and low-code capabilities to tackle even the most complex challenges across your security organization.
With the capacity to execute 25 million actions per day for a single customer—ten times faster than competing platforms—it prides itself as one of the most scalable security automation solutions.
Turbine isn’t just fast; it’s smart, adapting to your environment and evolving with your security needs. With the Swimlane Marketplace, you can easily tap into a modular, full-stack ecosystem to maximize automation and see a return on investment faster than you thought possible.
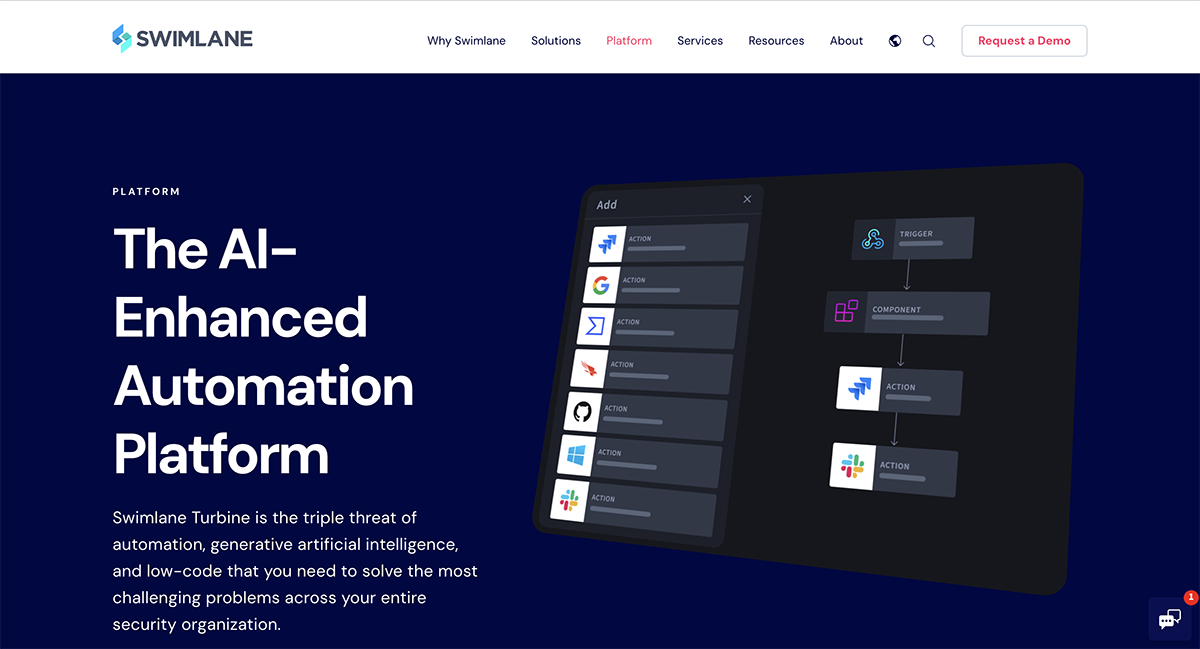
Here’s where Turbine really stands out against other platforms: it fills the gap between clunky traditional SOAR platforms and overly simplistic no-code solutions. If you’re looking to process millions of alerts daily, generate AI-assisted reports or deploy in a cloud-native or on-premises setup, Swimlane Turbine empowers your security operations to stay proactive and efficient.
Features
- No & Low-code Playbook Builder: Simplify automation with reusable components, a low-code studio and a human-centric design for greater visibility.
- Hero AI: Generate Python scripts, craft AI-driven prompts and summarize cases with Swimlane-hosted LLMs for secure, private data handling.
- Autonomous Integrations: Access infinite REST API integrations and an ecosystem-agnostic network with business logic embedded in playbook execution.
- Business Intelligence Applications: Gain visibility into SecOps, fraud, OT and compliance with real-time dashboards and advanced case management tools.
- Active Sensing Fabric: Handle millions of alerts daily with unmatched processing power and custom business logic for enrichment.
Pricing
Swimlane has four Enterprise pricing plans:
- Base
- Advantage
- Premium
- Enterprise
MSSP Pricing tiers include:
- Standard
- Plus
- Pro
- Elite
Contact sales to request the pricing for all tiers.
Rating
- Gartner Peer Insights: 4.8/5 (119 reviews)
- G2: 4.6/5 (44 reviews)
- Capterra: 4.0/5 (1 review)
6. Microsoft Sentinel

Best For: Teams needing a cloud-native SIEM and SOAR solution with powerful AI-driven threat detection capabilities.
Microsoft Sentinel is your go-to, cloud-native SIEM and SOAR solution designed to provide intelligent and comprehensive security for modern enterprises. Built on the power of Azure, it’s scalable, flexible and ready to tackle even the most complex security challenges.
Whether you’re managing a small business or a sprawling global operation, Sentinel collects, analyzes and responds to security data from every corner of your infrastructure—on-premises, in the cloud, or across hybrid environments.
Microsoft Sentinel integrates seamlessly with proven Azure services like Log Analytics and Logic Apps while tapping into Microsoft’s unparalleled threat intelligence. This gives your security team the tools to not only detect and respond to threats faster but also to anticipate and prevent them.
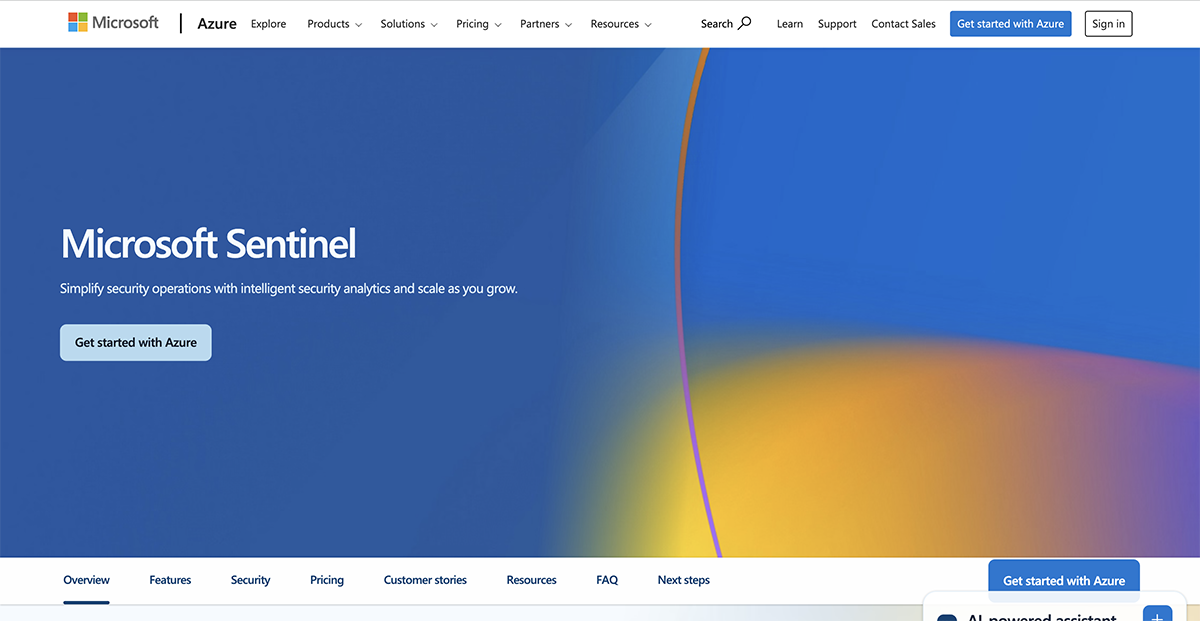
With advanced AI at its core, Sentinel helps you cut through the noise by minimizing false positives and grouping alerts into actionable incidents. Plus, it’s designed with flexibility in mind, so you can bring your own threat intelligence or take advantage of its robust, out-of-the-box capabilities.
Features
- Data Collection at Scale: Gather security data from all users, devices, applications and infrastructure across on-premises, multi-cloud and hybrid environments.
- Threat Detection: Reduce noise and detect sophisticated threats with advanced analytics, Microsoft's unmatched threat intelligence and integration with the MITRE ATT&CK framework.
- Interactive Investigations: Use AI-driven tools and visualizations to explore the scope and root causes of incidents and drill down into specific entities with an intuitive, graph-based interface.
- Proactive Threat Hunting: Stay ahead of potential threats with powerful hunting tools that allow you to analyze your environment before alerts are triggered.
- Automated Response Playbooks: Create playbooks with Azure Logic Apps to automate routine tasks and streamline responses to incidents, reducing resolution times and improving efficiency.
- Workbooks for Visualization: Leverage built-in and custom workbooks to create interactive dashboards and gain actionable insights into your security data.
- Seamless Integration with Azure Services: Enrich your security capabilities by connecting with Azure services like Microsoft Defender, Azure Active Directory and more.
Pricing
Microsoft Sentinel charges you based on how much data it analyzes and stores in your Azure Monitor workspace (including Analytics, Basic and Auxiliary Logs). Visit their pricing page to get more information about the different purchase options available to you or request a quote.
Ratings
Gartner Peer Insights: 4.3/5 (4 reviews)
G2: 4.4/5 (288 reviews)
Capterra: 4.5/5 (6 reviews)
What to Look for in a SOAR Platform?
Now that we’ve reviewed a list of SOAR tools and their capabilities, how do you know which SOAR product is right for your company’s needs?
When comparing SOAR solutions, there are many different factors you need to take into account.
According to Gartner, SOAR solutions must provide:
- Highly customizable workflow process management that enables repeatable automated tasks to be turned into playbooks that run in isolation or joined together into more sophisticated workflows.
- The ability to store (locally or in a third-party system) incident management data to support SecOps investigations.
- Manually instigated and automated triggers that augment human security analyst operators to carry out operational tasks consistently.
- A mechanism to collate and better operationalize the use of threat intelligence.
- Support for a broad range of existing security technologies that support improved analyst efficiency and act as an abstraction layer between the desired outcomes and the custom-made set of solutions in place in your environment.
To help you make an informed decision, here’s a comprehensive guide to help you evaluate the key features and considerations:
Integration Capabilities
How many out-of-the-box (OOTB) integrations are available and how deep is their functionality? Does the platform support custom integrations via SDKs or APIs? Are new integrations and updates free or offered as add-ons?
A SOAR platform should work seamlessly with your existing tools, creating an interconnected ecosystem of SIEMs, endpoint protection, threat intelligence feeds and ticketing systems.
Automation That Fits Your Needs
Customizable automation workflows are a game-changer for handling repetitive tasks like alert triage, data enrichment and response coordination. This keeps your team focused on high-priority threats.
Find out from your vendor:
- Can workflows and playbooks be customized to align with your unique security processes?
- Does the platform offer visual, drag-and-drop playbook builders?
- Are there prebuilt playbooks for common scenarios?
Ease of Use
A SOAR platform should simplify operations, not add complexity. Look for an intuitive design that shortens learning curves and boosts productivity.
You want to find out:
- Is the interface user-friendly for both technical and non-technical users?
- Does it offer live playbook monitoring and real-time dashboards?
- Can tasks and playbooks be easily shared or transferred across teams?
Advanced Threat Intelligence
Can the platform map external threat intel to internal incidents for faster investigations? Does it automate threat intel distribution to enforcement points in real time? Your SOAR platform should integrate threat intelligence sources to enrich alerts and guide decision-making.
Incident and Case Management
Incident lifecycle management is crucial for effective responses. The platform should provide tools for investigation, documentation and post-incident review. Be sure to ask these questions: does it include native case management or integrate with external tools? Can it reconstruct incident timelines and generate audit trails?
Deployment Flexibility
Does it support on-premises, cloud, or hybrid deployments? Is it designed for multitenancy with horizontal scalability and high availability? A SOAR platform must fit into your current infrastructure and scale as your organization grows.
Real-Time Reporting and Dashboards
Does the platform offer customizable dashboards for tracking specific KPIs? Can reports be generated in real-time to provide actionable insights during incidents? Does it support exporting reports in multiple formats for sharing with stakeholders?
Visibility into your operations is critical. A strong SOAR platform provides real-time dashboards and detailed reporting to track metrics like response times, threat trends and ROI.
Scalability and Long-Term Value
As your organization grows, your SOAR platform should keep pace without diminishing performance. Discuss scaling options and long-term costs upfront to avoid surprises later.
Here are important questions to ask about scalability:
- How does the platform handle increased workloads, such as more alerts or users?
- Does it offer horizontal scalability to accommodate growth across multiple teams or tenants?
- Are there long-term cost implications for scaling integrations, storage or automation workflows?
Pricing
Is pricing based on actions, endpoints or users? Are there add-on costs for additional integrations, users or features? Are discounts available for long-term commitments? Pricing models vary widely. Choose one that fits your budget and operational needs without hidden fees.
Professional Services and Support
Beyond features, strong vendor support can make or break your SOAR adoption. You should ask your SOAR vendors for the following after-sales support services:
- Deployment assistance for seamless onboarding.
- Playbook development tailored to your specific use cases.
- Training programs to maximize the platform’s value.
- 24/7 customer support via chat, email, or phone.
- Dedicated account managers for ongoing assistance.
- Access to knowledge bases, forums and regular health checks.
SOAR FAQs
The SOAR model in cybersecurity refers to Security Orchestration, Automation and Response. It’s a technology stack that helps security teams automate repetitive tasks, integrate disparate security tools and streamline workflows to respond to threats faster and more effectively.
No, SOAR is far from outdated. With the increasing volume and complexity of cyber threats, SOAR tools remain critical for modern security operations. Their ability to automate tasks, orchestrate across multiple tools and enable faster responses ensures their relevance in evolving cybersecurity landscapes.
SOAR in cybersecurity stands for Security Orchestration, Automation and Response. It empowers security teams to manage alerts, analyze threats and execute incident responses efficiently by leveraging automation and orchestration across various security tools.
Based on Gartner’s Peer Insights, the leading SOAR platforms include Palo Alto Networks Cortex XSOAR, Splunk Phantom, Cyware, IBM Security QRa2dar SOAR, Microsoft Sentinel and Swimlane. These platforms are known for their robust automation capabilities, seamless integrations with other tools and user-friendly interfaces that simplify complex security operations.
The security market, including SOAR, is experiencing significant growth as organizations prioritize automation and efficiency in combating advanced threats. Innovations in AI and machine learning are further enhancing SOAR platforms, making them indispensable for security operations centers (SOCs).
SOAR improves incident response by automating routine tasks like alert triage and log analysis, reducing response times and minimizing human error. It also provides centralized dashboards for better visibility and enables seamless collaboration across security tools, ensuring faster and more coordinated threat mitigation.
Threat Intelligence Management (TIM) in the SOAR context involves collecting, analyzing and applying threat data to enhance incident response. TIM integrates with SOAR platforms to automate the application of intelligence, enabling faster and more accurate responses to evolving cyber threats.
Splunk is primarily a SIEM (Security Information and Event Management) solution designed for log management and threat detection. However, it also offers SOAR capabilities through Splunk Phantom, which automates and orchestrates security operations, making it a hybrid solution for comprehensive security management.
Create Amazing Interactive Content Like a Pro with Visme
There you have it—everything you need to know about SOAR (Security Orchestration, Automation and Response). Whether you're a small team looking to boost efficiency or an enterprise aiming to stay ahead of advanced attacks, SOAR is a must-have for your SOCs. It not only empowers your team to do more with less, but it also elevates your organization’s security posture.
Having the right technology is just one part of the equation. To unlock the full potential of SOAR, your team needs clear documentation, effective training materials and visual guides to align on processes and workflows. That’s where Visme shines.
With Visme, you can create stunning, easy-to-follow resources like:
- SOPs and Playbooks: Visualize your automated workflows and incident response steps in professional, branded documents.
- Infographics: Visualize data flows, threat intelligence and key metrics to help your team grasp complex processes at a glance.
- Flowcharts: Map out decision trees and playbooks to ensure consistency across your SOC.
- Presentations: Train your team or onboard new members with visually engaging, interactive slides.
Visme’s intuitive editor, vast library of templates and an extensive collection of advanced features make it simple to turn complex security strategies into accessible resources.
By pairing your SOAR platform with Visme, you’re not just optimizing your security operations—you’re ensuring your team is equipped, informed and ready to respond.
Request a demo to see how Visme can help you create documentation, guidelines and resources that elevate your security operations.
Create Stunning Content!
Design visual brand experiences for your business whether you are a seasoned designer or a total novice.
Try Visme for free